Admin Settings
Perform basic settings to administer Key Manager Plus from the Settings section. Create accounts for other users, perform basic configurations such as mail server setting, proxy details, active directory integration, periodic backup schedule, and other tasks.
- User Management
- Integrate Active Directory and Import Users
- RADIUS authentication
- LDAP authentication
- Mail Server Settings
- Proxy Server Settings
- RESTful API
- Dashboard Settings
- Installing server certificate
- Privacy Settings
- Policy Configuration
- SSL Settings
- Change Password
- Ticketing System
- Notification Policy
- Integration with CMDB
- Domain Expiration
- Additional Fields
- Apply License File
1. User Management
1.1 User Roles
Key Manager Plus allows you to have two types of user roles. Administrator and Operator.
| Administrator | Operator | |||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Di | C | I | V | A | D | E | Di | C | I | V | A | D | E | |
| Manage User accounts (in Key Manager Plus) | NA |  |  |  |  |  | NA | NA |  |  |  |  |  | NA |
| Manage SSH Servers and Resource Groups |  |  |  |  |  |  | NA |  |  | NA |  |  |  | NA |
| Manage SSH keys and Key Groups |  |  |  |  |  |  |  |  |  |  |  |  |  |  |
| Manage SSH Users and User Groups |  |  |  |  |  |  |  |  |  |  |  |  |  |  |
| Manage SSL Certificates |  |  |  |  | NA |  |  |  |  |  |  | NA |  |  |
| Connect with remote SSH terminal |  |  (Only to user accounts assigned by the administrator) | ||||||||||||
| Schedule operations |  |  | ||||||||||||
Di — discover ; C — create ; I — import ; V — view ; A — assign ; D — delete; E-Export
1.2 User Addition
You can add users to Key Manager Plus and create an account for them to access the product in two ways:
- Manually add users
- Import users from Active Directory.
1.2.1 Add Users
To create a user,
- Navigate to the Settings >> User Management >> Users tab in the GUI.
- Click the Add User button.
- Enter the Login name, Password, and the E-mail Id of the user.
- Assign role for the new user - Administrator or Operator.
- If you are selecting the role for the new user as Administrator, you can select and save that.
- If you are assigning the Operatorrole to the user, you can select whether the user can access SSH user accounts and/or SSL certificates, and, these should be added manually. If you are assigning SSL certificates to the user, directly select the certificates. For SSH server selection, three options are available:
- Select Specific Users — Click the check boxes available next to a resource name to assign all the user accounts of that resource to the operator. Else, click the arrow next to the checkbox to expand the list of user accounts available in the resource and select individual user accounts to be assigned.
- Resource group — Select the group(s) to be assigned to the operator. The operator is provided access to only those SSH user accounts across all the resource(s) (of the selected resource groups), which have the same name as the login name of the operator.
- User group — Select the group(s) to be assigned to the operator. The operator is provided access to only those SSH user accounts available in the selected user group(s).
- You can simultaneously assign SSH user accounts, and SSL certificates to the same user (operator).
- Click Save.
A pop up message will confirm the addition of a new user to the database.
Note: Only operators need to be assigned the resources and groups for which they need access. Administrators are automatically provided with access to all resources and certificates associated with Key Manager Plus.
Generate user certificates
You can also create and sign certificates for Key Manager Plus users based on a root certificate. To generate user certificates,
- Navigate to Settings >> User Management >> Users tab.
- Select the user(s) for which you need to generate a certificate and click Sign.
- In the pop-up that opens, select the root certificate based on which the user certificate(s) need to be signed, specify the SAN and validity in days.
- By default, the user certificate inherits the same parameters as that of the root certificate. You can modify its details by unchecking the Use root certificate details check-box.
- Click Sign. Separate certificates are generated for the user accounts selected and are consolidated in Key Manager Plus' certificate repository.
You then have to deploy these certificates to their corresponding end-servers. Refer to this section of help for step-by-step explanation on certificate deployment.
1.2.2 Modify Users
To edit a user:
- Navigate to the Settings >> User Management >> Users tab in the GUI.
- Select a user and click the Edit User button.
- Modify the email id, assigned users list, or user role.
- Click the Update User button to update changes.
You will get a confirmation message that the changes to the user have been updated successfully.
2. Integrate Active Directory and Import Users
You need to carry out the following steps to import users from AD and assign them necessary roles and permissions in Key Manager Plus:
You can store any key file securely in the Key Manager Plus repository from the Key Store tab. From here, you can also edit the key details, update key file, keep track of previous versions of the key, store them in an organized manner, or export the keys, or previous versions to your system or mail address.
2.1 Importing Users
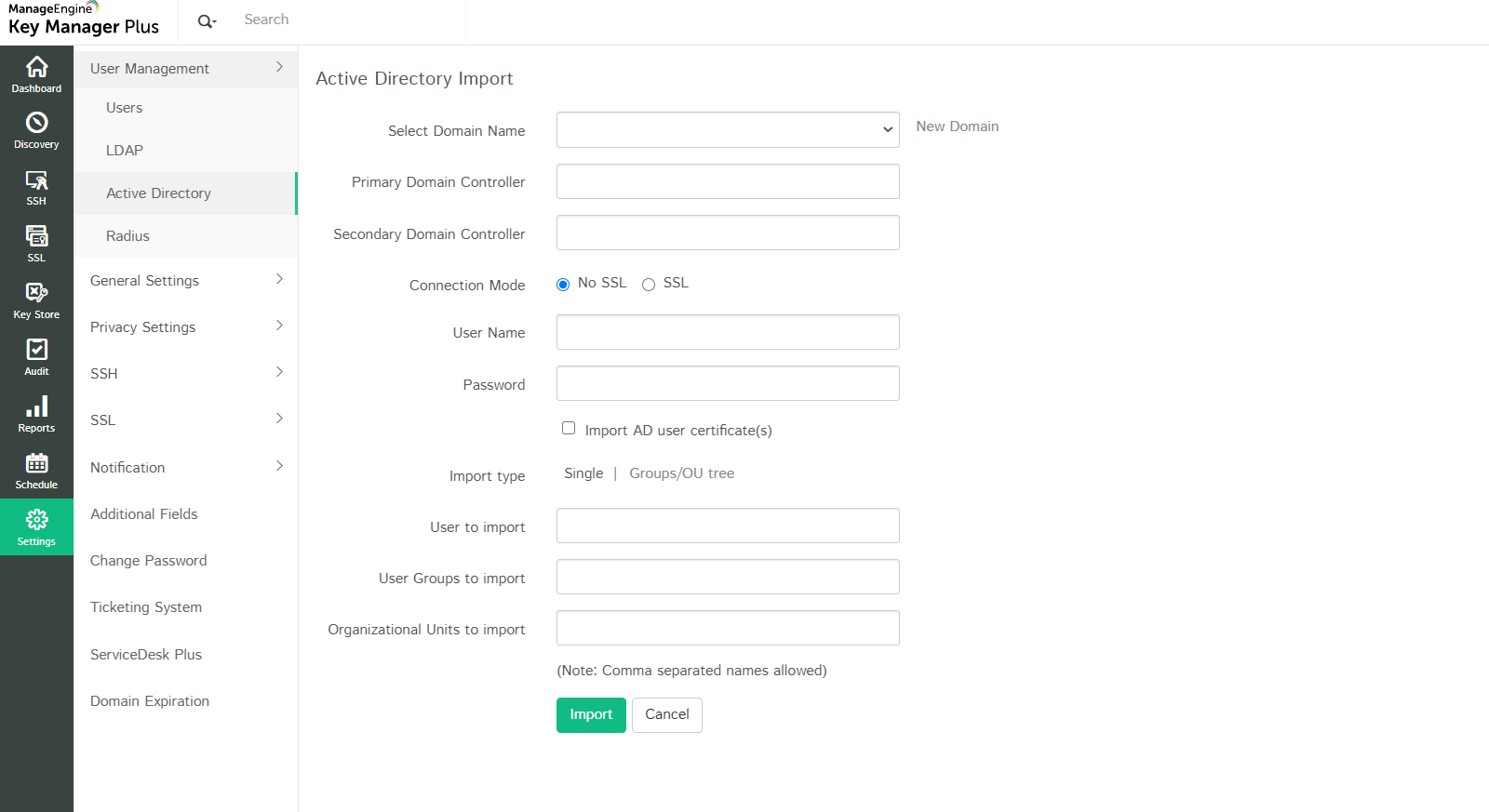
From the server in which it is running, Key Manager Plus automatically gets the list of domains available under the Microsoft Windows Network folder. You need to select the required domain and provide domain controller credentials.
To do this,
- Navigate to Settings >> User Management >> Active Directory.
- Select the required Domain Name, which forms part of the AD from the drop-down.
- Specify the DNS name of the Domain Controller. This domain controller will be the primary domain controller.
- In case, the Primary Domain Controller is down, Secondary Domain Controllers can be used. If you have secondary domain controllers, specify their DNS names in comma separated form. One of the available secondary domain controllers will be used. When you use SSL mode make sure the DNS name specified here matches the CN (common name) specified in the SSL certificate for the domain controller.
- Enter a valid user credential (User Name and Password) of an user account within the particular domain. Then enter the Users / User Groups / OUs that you want to import as comma separated values and click Import. To import user groups/OUs directly, choose Groups/OU tree Import type and select the required groups from the list.
- Also, Key Manager Plus provides an option to automatically discover SSL certificates in the Active Directory (AD) users as and when they are imported into Key Manager Plus. Enable the check box Import AD user certificate(s) to perform the discovery and import the certificates into the certificate repository of Key Manager Plus.
- For each domain, you can configure if the connection should be over an encrypted channel for all communication. To enable the SSL mode, the domain controller should be serving over SSL in port 636 and you will have to import the domain controller's root certificate into the Key Manager Plus server machine's certificate.
As mentioned above, to enable SSL mode, the domain controller should be serving over SSL in port 636. If the certificate of the domain controller is not signed by a certified CA, you will have to manually import the certificate into the Key Manager Plus server machine's certificate store. You need to import all the certificates that are present in the respective root certificate chain — that is the certificate of the Key Manager Plus server machine and intermediate certificates, if any.
To import domain controller's certificate into Key Manager Plus machine's certificate store: (you can use any procedure that you normally use to import the SSL certificates to the machine's certificate store. Refer to the example given below)
- In the machine where Key Manager Plus is installed, launch Internet Explorer and navigate to Tools >> Internet Options >> Content >> Certificates.
- Click Import.
- Browse and locate the root certificate issue by your CA.
- Click Next and choose the option Automatically select the certificate store based on the type of certificate and install.
- Again click Import.
- Browse and locate the domain controller certificate.
- Click Next and choose the option Automatically select the certificate store based on the type of certificate and install.
- Apply the changes and close the wizard.
- Repeat the procedure to install other certificates in the root chain.
Key Manager Plus server can now communicate with this particular domain controller over SSL. Repeat these steps for all domain controllers to which you want Key Manager Plus to communicate over SSL. Note that the DNS name you specify for the domain controller should match the CN (common name) specified in the SSL certificate for the domain controller.
- By default, Key Manager Plus will populate all the OUs and groups from AD. If you want to import only a particular user, enter the required user name(s) in comma separated form.
- Similarly, you can choose to import only specific user groups or OUs from the domain. You can specify the names in the respective text fields in comma separated form.
- Click Import. Soon after hitting this button, Key Manager Plus will start adding all users from the selected domain. During subsequent imports, only the new users entries in AD are added to the local database.
- In the case of importing organizational units (OUs) and AD groups, user groups are automatically created with the name of the corresponding OU/AD group.
Important Note:
Groups/OUs too large to display
When you have a large number of groups or OUs in the domain controller, specifically when the number exceeds 2500, Key Manager Plus will not display them in the GUI. In such cases, you will see the message Groups too large to display / Organizational Units too large to display. When this happens, you have to specify the groups or OUs that are to be imported alone, instead of getting all the groups / OUs in the display.
- What will be role of the users imported from AD, in Key Manager Plus? The users added to the Key Manager Plus database will have the role as Operators.
- Can I handle both AD and non-AD permissions to login to Key Manager Plus? Yes. You can use both your AD and local (non-AD) passwords to login to the application. The choice can be made in the GUI login screen itself.
2.2 Assigning Roles
All the users imported from AD will be assigned the Operator role by default. To assign specific roles to specific users and/or to assign SSH user accounts of discovered resources, refer the Modify Users page of the help document.
You will get a confirmation that the user has been deleted successfully.
3. Radius Authentication
Click here to learn more about Radius Authentication.
4. LDAP Authentication
Click here to learn more about LDAP Authentication.
5. Mail Server Settings
After installation, you need to carry out certain basic settings. The first setting is related to configuring the mail server to let Key Manager Plus send emails directly from within the application without the need of an external mail client. You need to configure the SMTP server details as given in the steps below. Key Manager Plus users can be notified regarding schedules, policy enforcements, and reports, only through email. The same settings are also used while exporting the certificate, digital key files via email; and also for the Forgot Password option in the login page.
To set/modify the mail server settings:
- Navigate to the Settings >> General Settings >> Mail Server tab in the GUI.
- Enter the server name and specify the port used for communication. Enter the User Name and Password for authentication.
- Enter the from and to mail addresses.
- Click the Test Mail button to send a test mail to the address specified, and verify the settings.
- Click the Save button.
You will get a confirmation that the mail server settings have been updated.
6. Proxy Server Settings
You then need to specify how you want to connect to the Internet - directly or over a proxy.
To set/modify the proxy server settings:
- Navigate to the Settings >> General Settings >> Proxy Server tab in the GUI.
- You can connect to the Internet either directly or using a proxy server.
- If you choose to connect using proxy server, enter the details of the server, and the user credential.
- Click Save.
You will get a confirmation message that the proxy server settings have been updated.
6.1 SNMP Settings
Key Manager Plus facilitates raising SNMP traps to management systems within your network for various key and certificate management operations performed from within the application. On the occurrence of a configured operation, an SNMP v2c trap is sent to the specified host and port. The varbinds include the name of the user who operated, date and time and the reason of the operation that resulted in the event.
To configure your SNMP server details,
- Navigate toSettings >> General Settings >> SNMP in Key Manager Plus web interface.
- Specify the hostname of the SNMP manager, port number and specify the SNMP community string.
- Click Save.
You will get a confirmation message that the SNMP server details have been configured.
6.2 Syslog settings
You can configure Key Manager Plus to generate and send RFC-3164 compliant Syslog messages to a dedicated server and port within your network. Syslog notification can be configured for the occurrence of key / certificate expiration, and for various other key / certificate management operations performed from the product.
To configure Syslog settings,
- Navigate to Settings >> General Settings >> SysLog Settings in Key Manager Plus web interface.
- Specify the IP address of the syslog server and the port number.
- Click Save.
You will get a confirmation message that the Syslog server details have been configured.
7. RESTful API
Click here to learn more on RESTful API.
8. Dashboard Settings
Since either or both of SSH keys and SSL certificates can be managed by a user, you can customize the Dashboard to reflect the details of only SSH keys, or SSL certificates, or both.
To customize the dashboard details:
- Navigate to the Settings >> Dashboard Settings tab in the GUI.
- Select the SSH, SSL, or Both radio button from the Dashboard type options to display the respective details on the dashboard.
- Click Save.
You will get a confirmation message that the configuration settings have been updated.
9. Installing Server Certificate
Click here to learn more about installing server certificates.
10. Privacy Settings
Click here to learn more about privacy settings.
11. Policy configuration
Key Manager Plus allows you to create a high level policy on SSH keys management. You can specify whether to retain or overwrite the existing keys. That means, when Key Manager Plus creates new keys if they are to be appended to the existing ones or they should be deleted. The second option helps you to remove all existing keys and have a fresh start. Your SSH environment will have only the keys that were generated by the Key Manager Plus. Key Manager Plus carries out these changes in the authorized_keys file directly.
From the Policy configuration tab in the GUI, you can set the option for adding keys to the authorized_keys file. You can choose from:
- Append — Allows you to retain existing keys as well the new ones deployed by Key Manager Plus.
- Overwrite — Removes all existing public key information from the authorized keys file and retains the public keys deployed from Key Manager Plus only. This is what we call as clean start.
To change the policy configuration:
- Navigate to the Settings >> SSH >> Policy Configuration tab in the GUI.
- Select to either Append or Overwrite the keys.
- Click Save.
You will get a confirmation that the policy configuration settings have been updated.
12. SSL Settings
Key Manager Plus provides certain settings exclusive to SSL related operations that can be customized based on user requirements. They are:
12.1 Vulnerability Scan
- Key Manager Plus provides users with the option to enable or disable the SSL vulnerability tasks created in schedules.
- There is an option to enable or disable SSLv3 protocol in Key Manager Plus server.
Note: The SSLv3 protocol should be enabled in Key Manager Plus server in order to perform the SSL vulnerability scan in target resources. By default, this setting is turned off.
12.2 Certificate Renewal
Key Manager Plus provides an option to automatically renew SSL certificates issued by Microsoft Certificate Authority and certificates self-signed from within the Key Manager Plus UI. When enabled, the corresponding certificates are renewed according to the recurrence time specified, and updated in Key Manager Plus certificate repository.
Note: For successful Microsoft CA auto renewal, ensure that the domain administrator account is used as Key Manager Plus service logon account.
12.3 Excluded Certificates
Key Manager Plus allows users to exclude specific SSL certificates from being imported into the certificate repository during discovery or manual addition.
To list a certificate that needs to be excluded:
- Navigate to Settings >> SSL >> Excluded Certificates.
- Click Add.
- Specify the common name, certificate serial number, reason, and click Save.
- The specified certificate is excluded from being imported into Key Manager Plus certificate repository during discovery / manual addition.
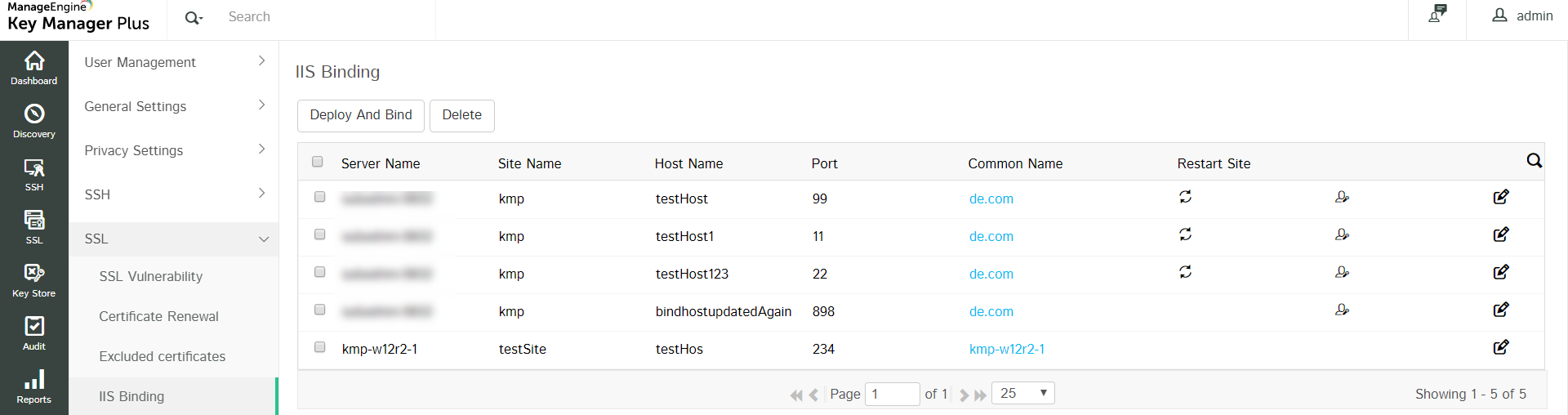
12.4 IIS Binding
Key Manager Plus allows users to deploy SSL certificates to the IIS server and also perform IIS binding. Click here for detailed steps on IIS binding. Once the server details are saved in the SSL tab, they will also be available in the Settings page. To deploy and bind certificates in bulk, follow the below steps:
- Navigate to Settings >> SSL >> IIS Binding.
- The details of servers to which you have deployed certificates will be listed here. Click the Edit icon beside a server and edit attributes such as Path, Site Name, Host Name, Port and Certificate. You cannot edit the Server Name. Select the Restartsite checkbox to restart the site automatically and click Save.
- Select multiple servers by clicking the checkboxes beside them and click Deploy And Bind from the top bar.
Now, the SSL certificates will be deployed to the associated server and IIS binding to the specified site will be complete.
13. Change Password
Users having a local account with Key Manager Plus, can change their own password and email ID. The Change Password tab facilitates this.
To change login password:
- Go to Settings >> Change Password tab in the GUI.
- Enter the old password.
- Enter new password.
- The new password will NOT be emailed. Take care to remember your new password. If you forget your password, use the Forgot password link available in the login page of Key Manager Plus to reset your password.
- Confirm the new password.
- Click Save.
13.1 Delete Users
To delete the users:
- Navigate to Settings >> User Management >> Users.
- Select the user you would like to delete and click the Delete User button.
14. Ticketing System
Click here to learn more about Ticketing System Integration.
15. Notification Policy
You can set up to get notified via email, syslog messages or SNMP traps in case of any of the following cases:
- If SSL certificates are expiring within a specified number of days.
- If domain names are about to expire within a specified number of days.
- If SSH keys are not rotated for more than a specified number of days.
- For certificate management operations performed from within the application.
- If PGP keys are expiring within a specified number of days. Click here to learn more about PGP keys.
Note: Notifications regarding PGP key expiration will be sent via email only.
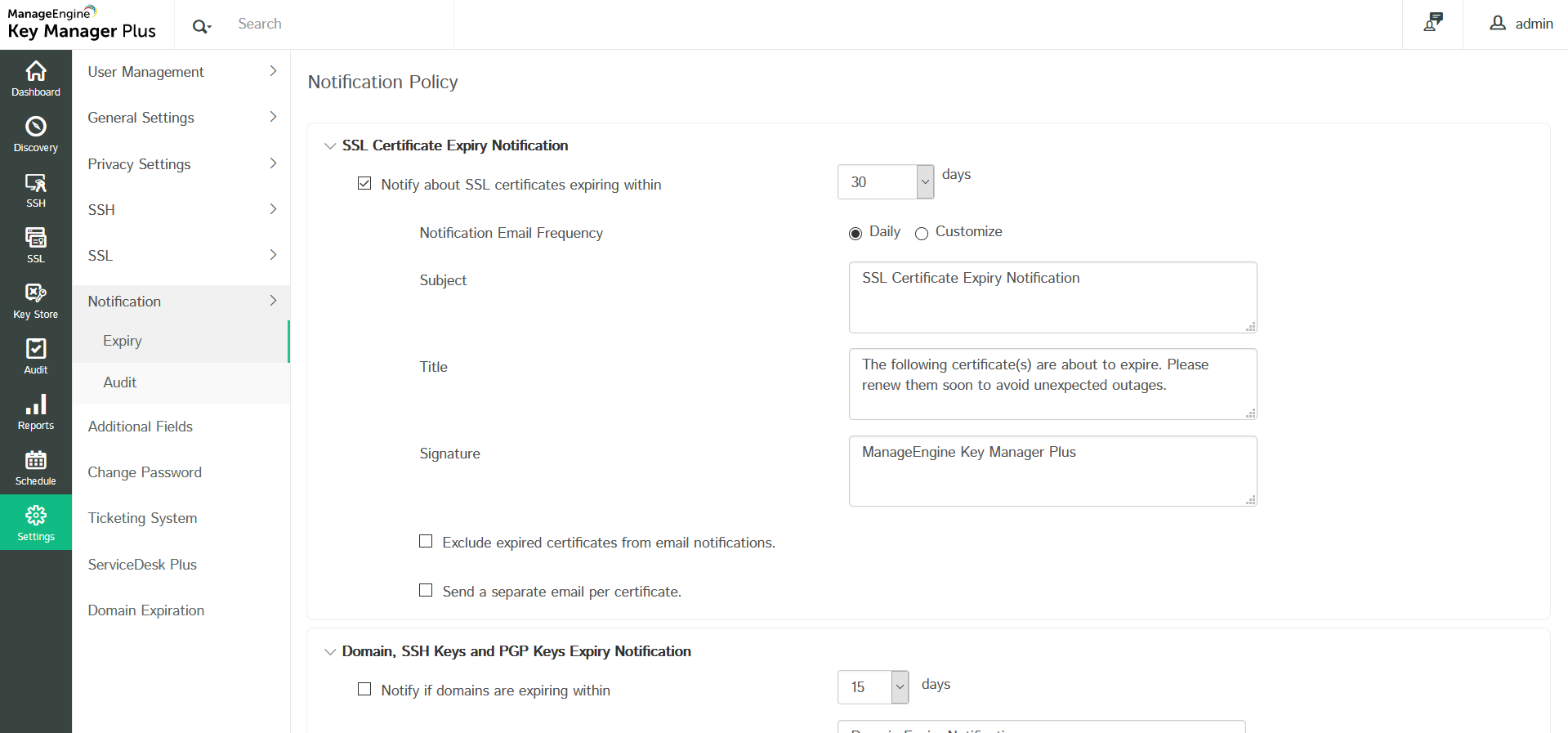
To set/modify expiry notification settings:
- Navigate to the Settings >> Notification >> Expiry tab in Key Manager Plus web interface.
- To enable SSL certificate expiry notifications, select the Notify about SSL certificates expiring within checkbox. Choose a value for days. You will get notified about only those certificates whose expiry dates fall within the period (number of days) you enter.
- Notification Email Frequency: Choose to receive notifications either Daily or Customize your notifications.
- If you choose to Customize, set the Interval (in days) to notify about the to-be-expired certificates.
- Select the Email certificates on every schedule if expiry is less than option if you want to receive notifications on all schedules irrespective of the above-set interval.
- Select Exclude expired certificates from email notifications to not get notified about expired certificates.
- Select Send a separate email per certificate if you want to customize each email with unique subject, title, etc.
- You can also choose to get notifications regarding domain name expiration, PGP key expiration or SSH key rotation failure for the configured time period or both by selecting the respective check-boxes. Expiring SSL certificates, and the SSH keys that were not rotated within the specified days are notified during the mentioned Recurrence Time.
- You are also allowed to edit the Subject, Title and Signature of your email-notifications.
- You can choose to be notified in two ways:
- E-mail — Enter the from and to addresses. To enter mail server details, go to the Mail Server Settings tab.
- Syslog — Navigate to Settings >> General settings >>Syslog settings to mention the IP address of the server and the port to which the syslog is to be delivered.(Refer to the format below)
- After filling in the details, click Save.
15.1 Syslog Format
SSH
<190> Key_Name:172.21.147.130_test123_id Days_Exceeded:0 Modified_On:2016-02-16 17:41:24.008
SSL
<190> Parent_Domain: manageengine.com Included_Domain: kmp.com Days_to_Expire: 100 Expire_Date: 5.08.2017
Note: The number of days specified in the SSH key rotation and SSL certificate expiry notification policy will be applied to the dashboard settings also.
To set/modify audit notification settings:
- Navigate to the Settings >> Notification >> Audit tab in Key Manager Plus web interface.
- You can customize the alert notifications to be received for different types of operations performed in Key Manager Plus.
- Choose the type of notification to be received by enabling the check-boxes beside each operation.
- For SNMP and Syslog notifications, make sure you have already configured the server details under Settings >> General Settings >> SNMP / SysLog settings.
- For email notifications, you can either choose to notify all the administrator users or just a specific set of email IDs by enabling the respective check boxes.
- Once you have specified the choices, click Save.
16. Integration with CMDB
Click here to learn more about CMDB integration.
17. Domain Expiration
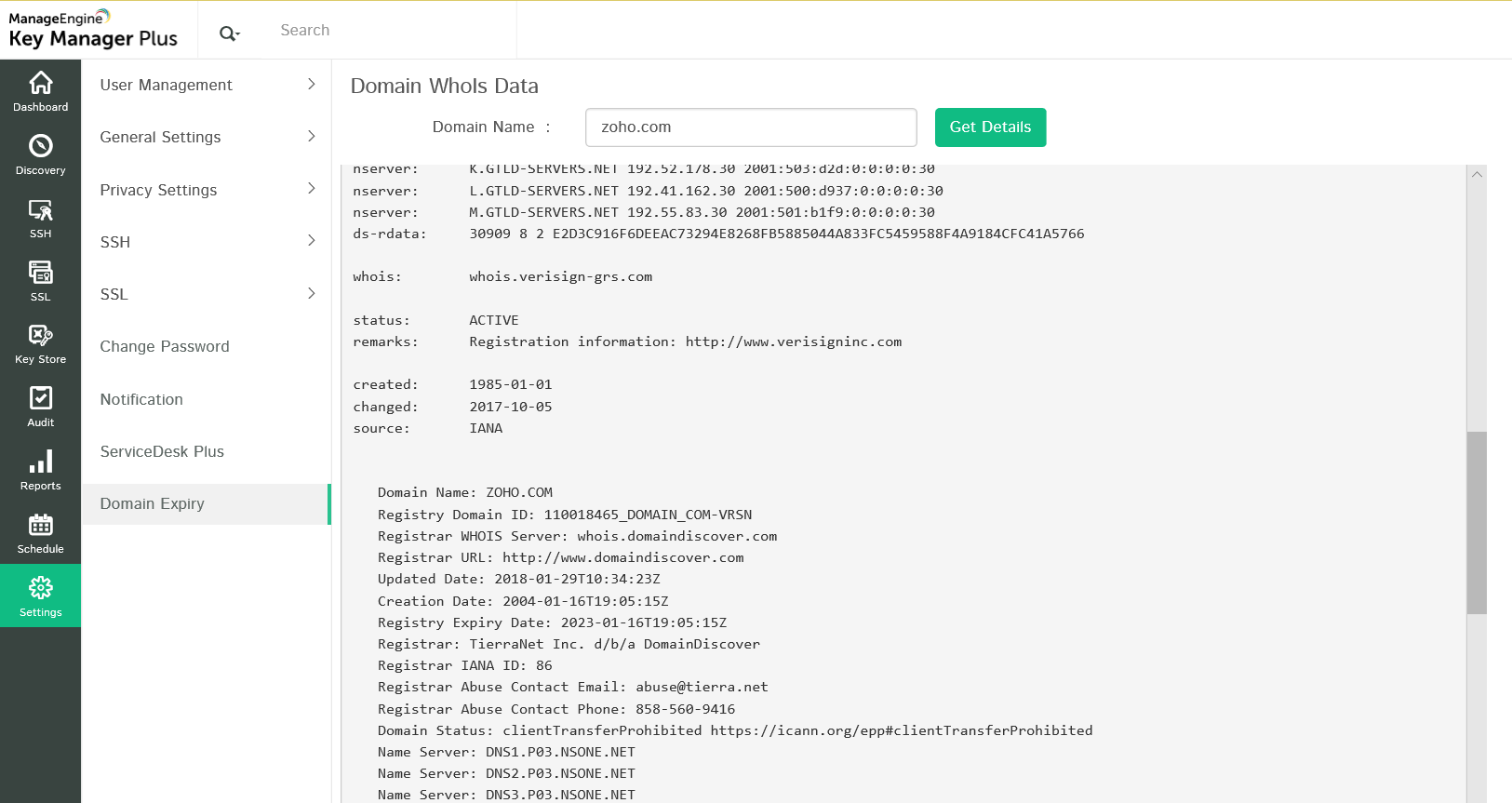
Key Manager Plus has an in-built WHOIS look up tool that helps administrators query and obtain information about any registered domain name such as ownership details, date of registration & expiration, IP address history and more.
To access the WHOIS look up tool,
- Navigate toSettings >> Domain Expiration.
- In the window that opens, enter the domain name for which you want to obtain the details (in terms of a top-level domain or sub domain of a top-level domain).
- Click Get Details. The details about the domain are displayed in the dialog box that opens below.
18. Additional Fields
Click here to learn more about additional fields.
19. Apply License File
When you purchase Key Manager Plus, you will get a product license key. You can apply the license key by following the steps below:
- On the top right hand corner of the GUI, you will find your account information. Click that.
- Select the License option.
- Click the Update License button in the License Details pop-up window.
Upload the license file supplied to you by Key Manager Plus.