Configuring Landing Servers for Data Center Remote Access
Overview
Typically, data centers forbid direct access to remote devices via SSH or Telnet connections. So, a data center admin trying to establish connection with a remote device should initially establish connection with a landing server and then 'hop' to the target device through that landing server. In some cases, he should have to make multiple such 'hops' before finally establishing connection with the required server. In each step of the remote access process - from the initial landing server to subsequent hops towards the target server - connection is established through Secure Shell (SSH), which essentially means the admin should provide the appropriate ssh keys associated with the servers at every level untill connection is established with the target server. Keeping track of all the keys is daunting and often leads to errors and inaccuracies.
Key Manager Plus has simplified this entire data center remote access management. You can use Key Manager Plus to effectively launch direct connections to IT equipments in the data centers, overcoming access barriers created by network segmentation while adhering to data center access protocols. Key Manager Plus also supports complete key management of those remote devices.
Using the landing server arrangement, you can make multiple 'hops' to remotely access an IT equipment in your data center. Configuring landing server for a resource is a one time process. Once you've appropriately configured the landing server for a remote device, Key Manager Plus automatically makes the 'hops' and establishes connection with the target device in a completely automated fashion.
Configuring landing servers - Summary of steps
Following are the steps involved in configuring landing servers:
- Step 1: Discover the resource
- Step 2: Supply credentials
- Step 3: Configure the resource as landing server
- Step 4: Associate target device with the landing server
- Step 5: Establish direct connection with the target device
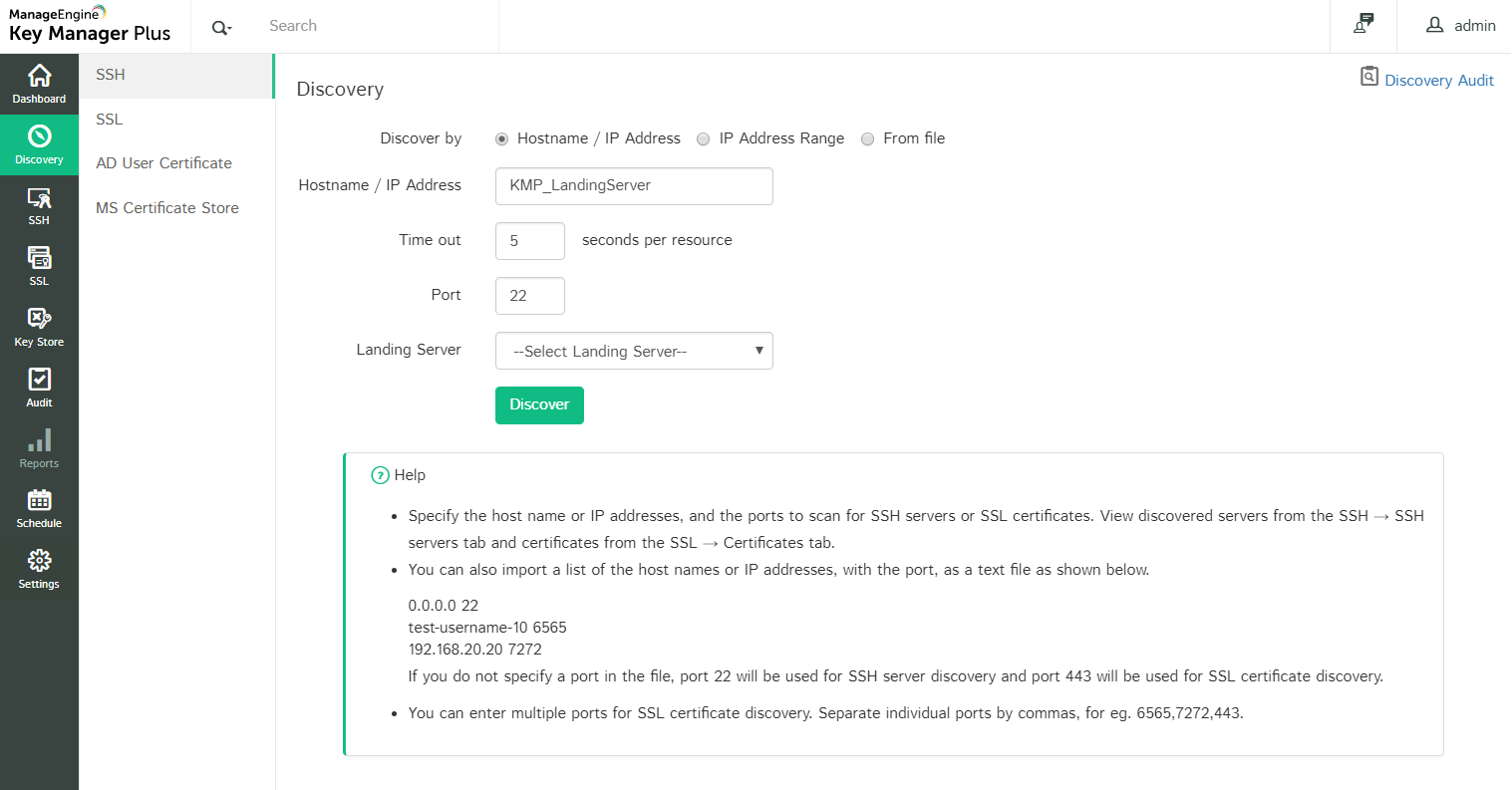
Step 1: Discover the resource
The first step is discovering the resource that has to be configured as a landing server. The resource discovery process is similar to that of normal SSH discovery.
- Navigate to Discovery --> SSH
- Choose the Hostname / IP Address radio button and provide the hostname or IP address of the server that is to be configured as a landing server
- Click Discover
- You can then view the discovered server under SSH --> SSH Servers
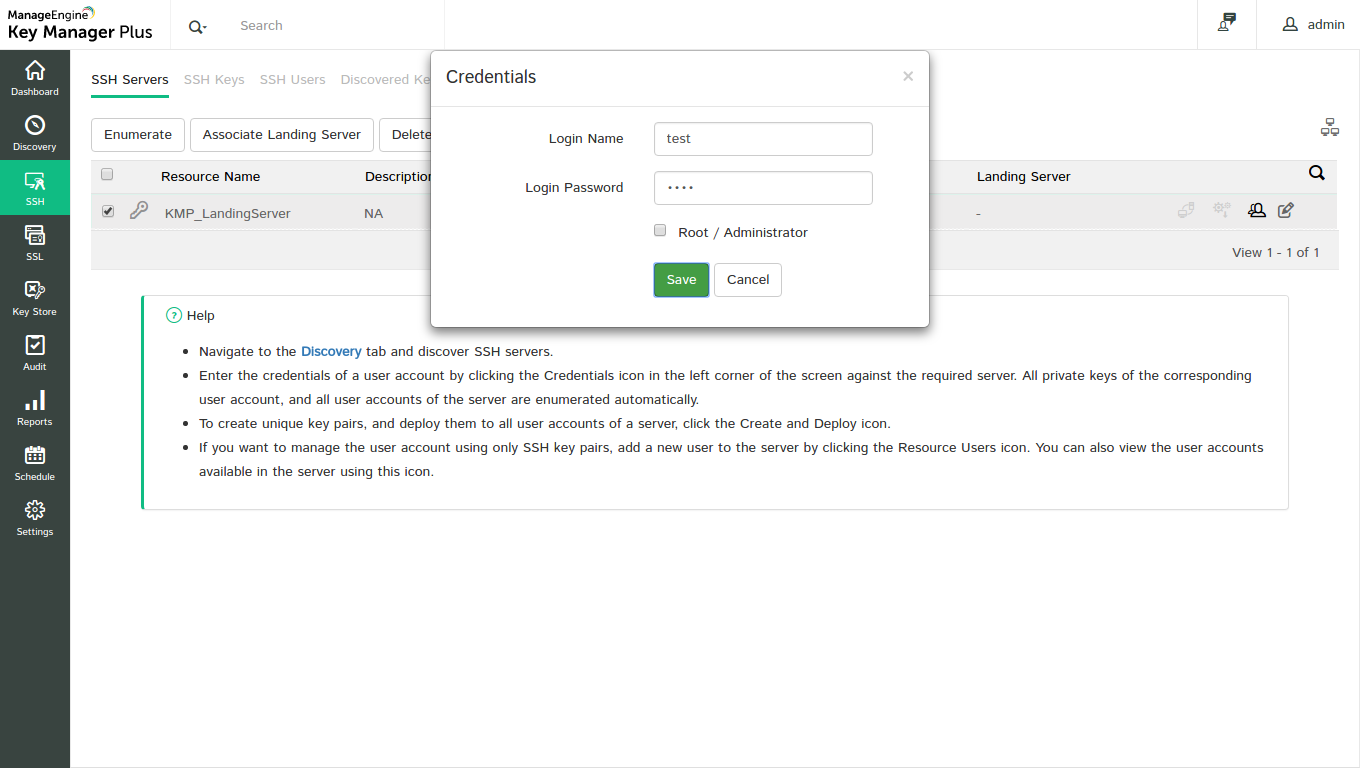
Step 2: Supply credentials
Click the ( ) icon beside the server name and provide the credentials (username / password) of the appropriate user account associated with the server.
) icon beside the server name and provide the credentials (username / password) of the appropriate user account associated with the server.
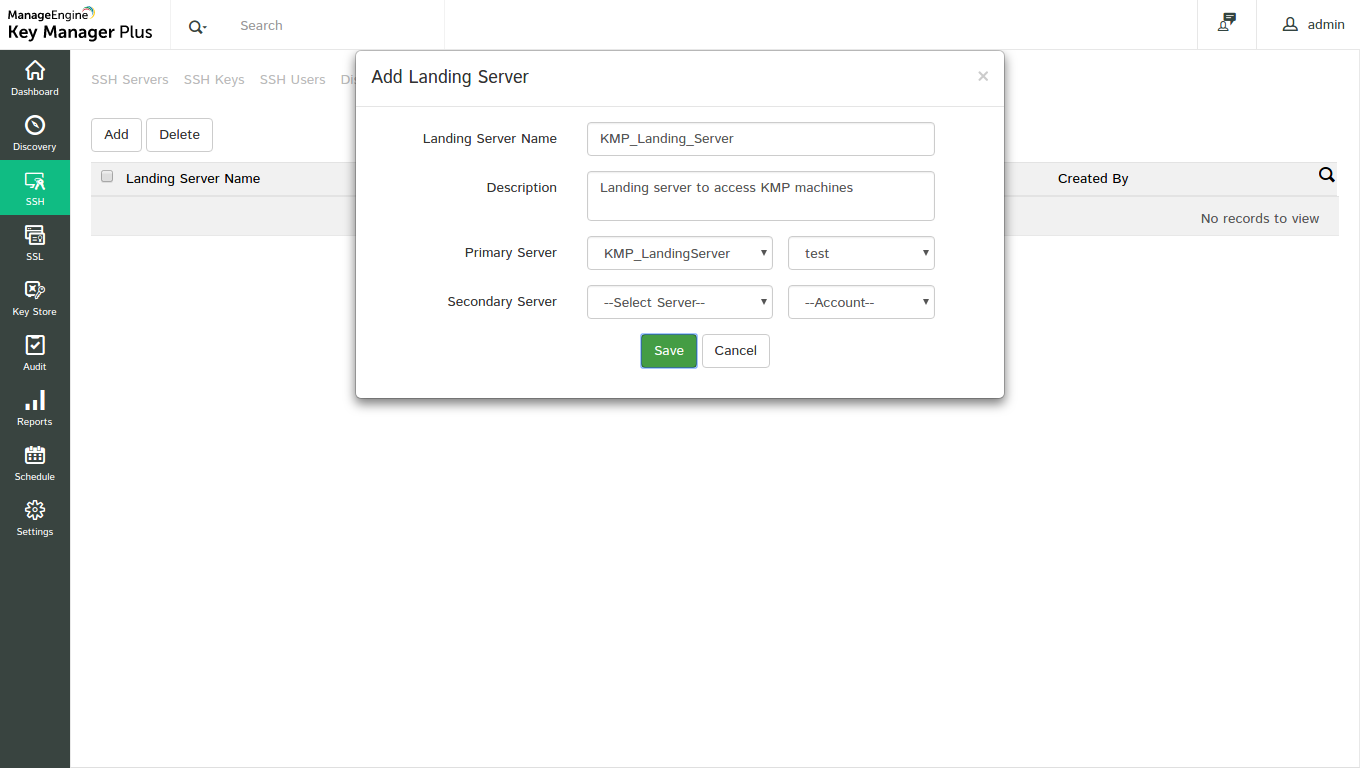
Step 3: Configure the resource as landing server
You then have to configure the discovered resource as a landing server. To do this,
- Navigate to SSH --> Landing servers --> Add
- Provide a name for the landing server, description, and then assign the resources
- You can assign a maximum of two resources to a landing server, thus establishing multiple connection paths. This is particularly helpful in cases when the primary server is down and you are not able to establish connection with the target device.
- Choose the required resource for primary and secondary servers from the drop-down and the appropriate user account and then click Save.
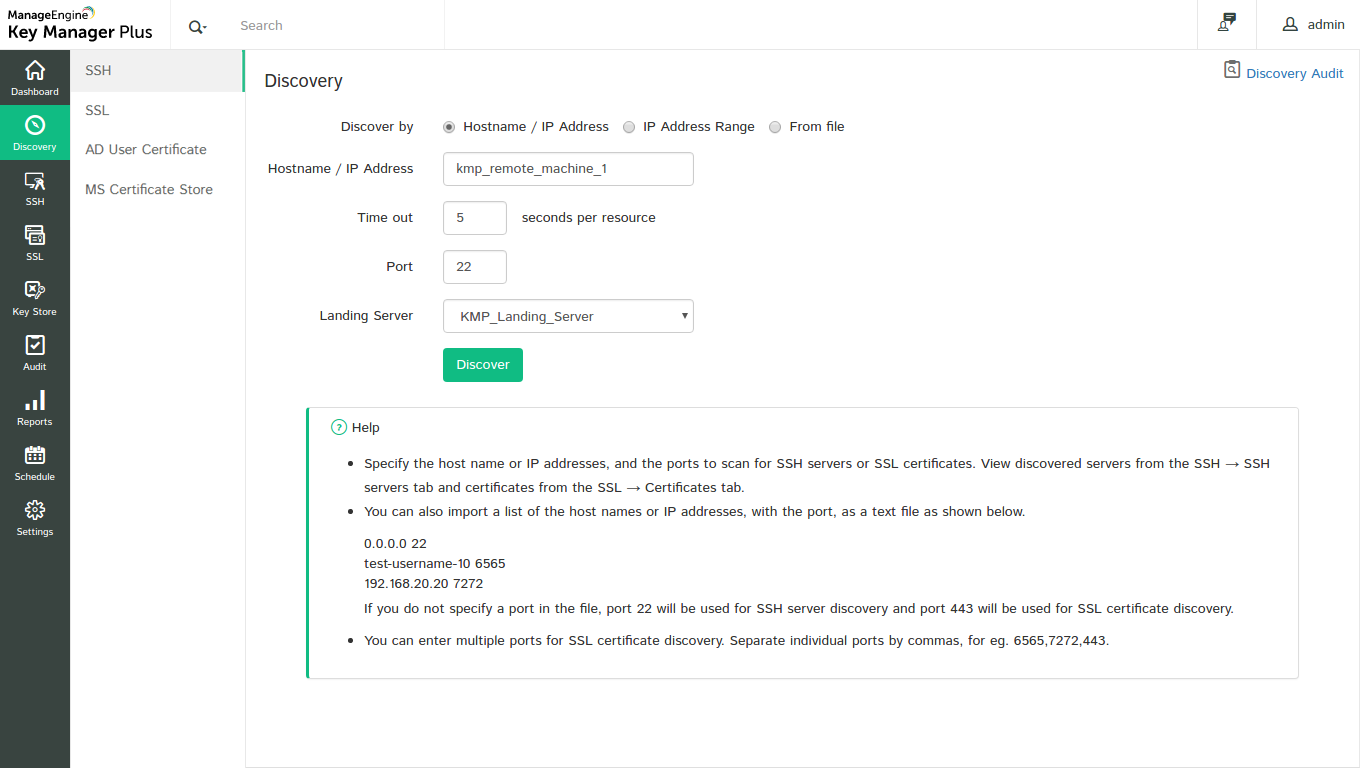
Step 4: Associate target device with the landing server
The next step is associating the required remote device with the landing server. The remote devices are not directly reachable, and establishing connection with these devices can be done only through the landing servers. To associate a remote device to the landing server,
- Navigate to Discovery--> SSH.
- Provide the Hostname / IP address of the target device, choose the landing server that you want to associate with the device from the drop-down and click Discover.
- You will see that the required resource is discovered for which the connection path is established through the landing server.
Step 5: Establish connection with the target device
Now that the target device has been associated with a landing server, you can perform key management operations on the target device like on any other device. Key Manager Plus automatically establishes the connection path and connects you to the device.
Quite often, you need to perform multiple 'hops' in order to connect to a remote device. Let's consider the scenario below.
KMP Server ---> Server 1 ---> Server 2
You initially discover 'Server 1' which is within the scope of your network, and then discover 'Server 2', which is the target server through Server 1 (which acts as landing server).
KMP Server ----> Server 2 ---> Server 3
After establishing connection with 'Server 2', you then have to connect to Server 3 (target server in this scenario) through 'Server 2' which is now to be configured as a landing server for reaching 'Server 3'.
You can then perform key management operations directly in the target servers like you would do for any other server.