Find Azure sign-in risks
Track all Azure AD logon activities and scrutinize various parameters, including the reputation of the IP address, location parameters, sign-in patterns, etc., to detect and remediate the sign-in security risks in Azure AD.
Stepping up Azure AD risk detection with ADAudit Plus
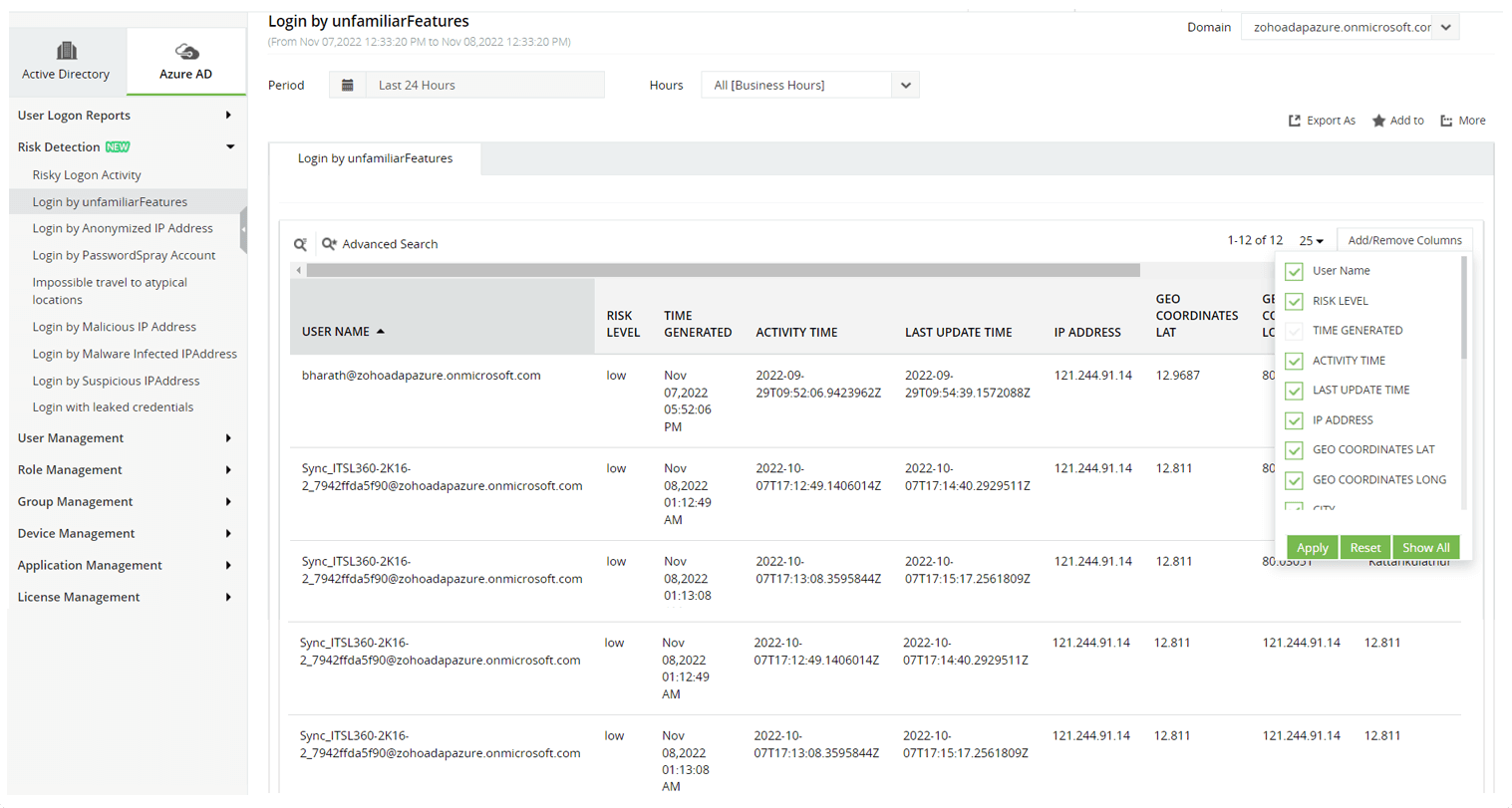
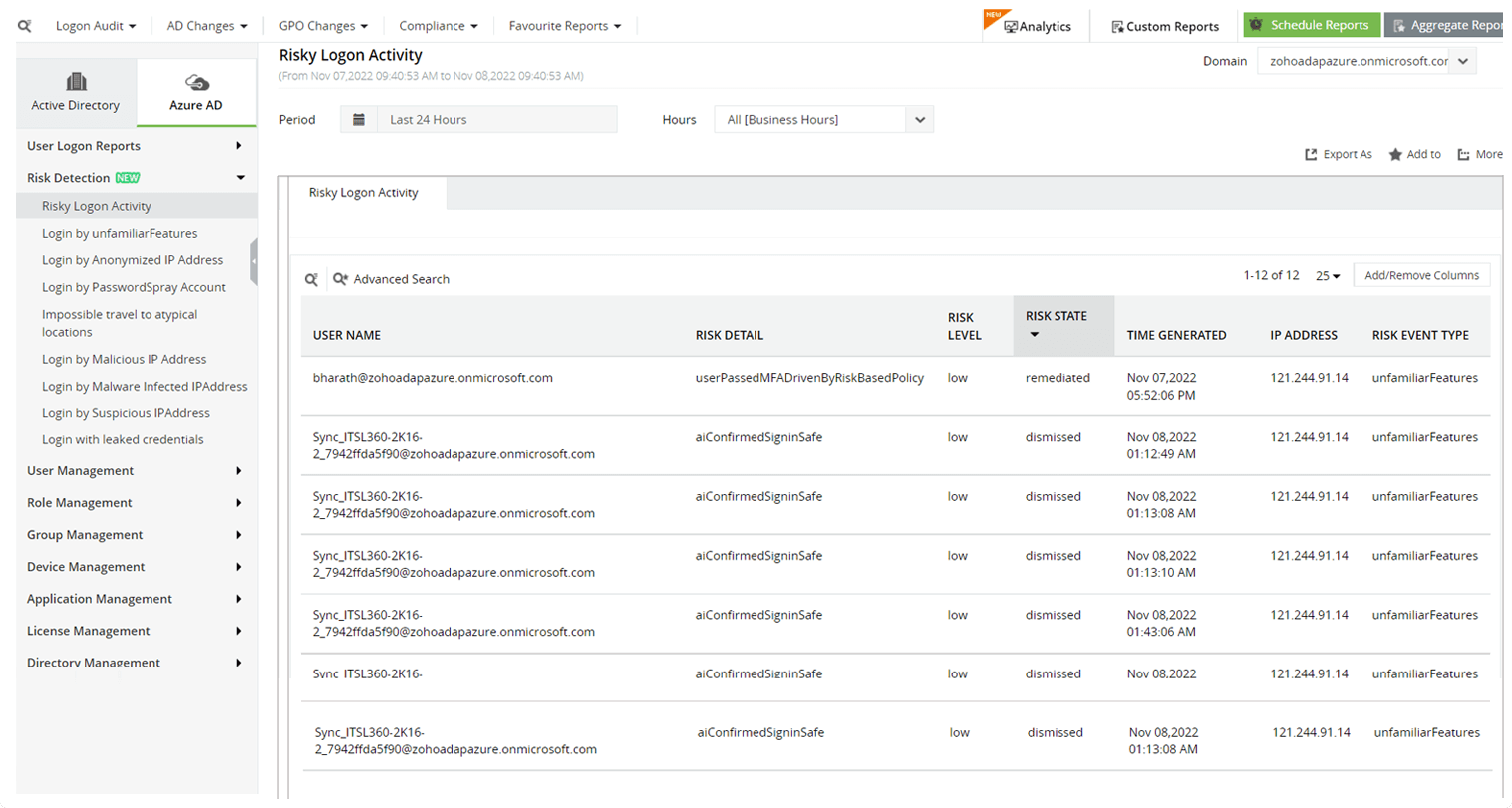
Track risky logon activities
Identify users whose suspicious logon activities risk your organization's Azure AD security. Generate reports on the risk level of the action, logon time, IP address, and more.
Employ hybrid AD security
Detect threats to your hybrid environment by analyzing suspicious logons across on-premises AD with user behavior analytics (UBA) and across the cloud using an Azure AD premium license.
Spot unauthorized sign-ins
Find multiple users who sign in using the same credentials by identifying two sign-ins from the same account that originate from geographically distant locations.
Track weak sign-in attempts
Monitor unsound activities such as sign-in attempts using expired, old, or weak passwords. Also, identify users who use their username as a part of their password.
Painless diagnosis and mitigation of sign-in risks in Azure AD
Track unsafe logon activities
Keep a close eye on sign-ins from IP addresses that either have a low reputation or a high logon failure rate due to the repeated use of invalid credentials.
Remediate password spray attacks
Identify logons using credentials that are simultaneously employed in a password spray attack, and initiate a threat response to disable the user accounts and limit the damage.
Discover the use of unsecured credentials
Trigger instant email and SMS alerts on discovering logons made by authorized personnel whose logon credentials have been leaked and shared on public sites, the dark web, etc.
Find malicious insiders
Flag users who deliberately try to conceal their sign-in information, such as device, location, IP address, etc., which could indicate a malicious insider.
Kick-start Azure sign-in risk detection and analysis with ADAudit Plus
Other solutions offered by ADAudit Plus section
Audit changes
Receive real-time notifications on changes occurring across both on-premises and Azure Active Directory.
Track user logons
Gain complete visibility into user logon activity, spanning from logon failures to logon history.
Troubleshoot account lockouts
Detect lockouts instantly and know their root cause by tracking down the source of authentication failure.
Monitor privileged users
Get a consolidated audit trail of administrator and other privileged user activities.
Audit Windows servers
Monitor local logon/logoff activities; changes to local users, groups, user rights; and more.
Track employee productivity
See the amount of time employees spend at their workstations.
File server auditing
Audit all file accesses across Windows file servers, failover clusters, NetApp, and EMC environments.
File permissions auditing
Audit all file and folder permission changes. Know who made those changes, when, and from where.
File integrity monitoring
Monitor and alert on unwarranted file accesses or modifications with real-time change auditing.
File change monitoring
Gain instant visibility into all modifications and failed access attempts made to your critical files.
Compliance requirements
Generate out-of-the-box compliance reports for regulations such as HIPAA, PCI DSS, GDPR, and more.
Forensic analysis
Investigate security incidents faster with actionable and accurate audit data.
Windows server auditing
Audit and monitor all user actions across the Windows server environment in real time.
Removable device auditing
Monitor usage of removable storage devices, such as USBs, and report on their file activities.
Printer monitoring
Monitor printer usage to find out who printed what critical files over the Windows network.
ADFS auditing
Monitor and report on both successful and failed ADFS authentication attempts in real time.
Audit process tracking
Track critical process creation and termination events with details on who initiated it and when.
File integrity monitoring
Monitor and alert on unwarranted file accesses or modifications with real-time change auditing.
Workstation auditing
Audit, alert, and report on critical user activities across workstations in real time.
Logon and logoff monitoring
Monitor and track all users' logon and logoff activities to spot anomalous user sessions.
File integrity monitoring
Ensure file integrity by keeping track of changes made to the system, program files, and more.
User login history monitoring
Track, record, and maintain an audit trail of all users' login history details.
Audit process tracking
Track critical process creation and termination events with details on who initiated it and when.
Employee time tracking software
Measure your employees' productivity by keeping track of their idle time and actual work hours.