Want to discover bad actors
lurking in the shadows?
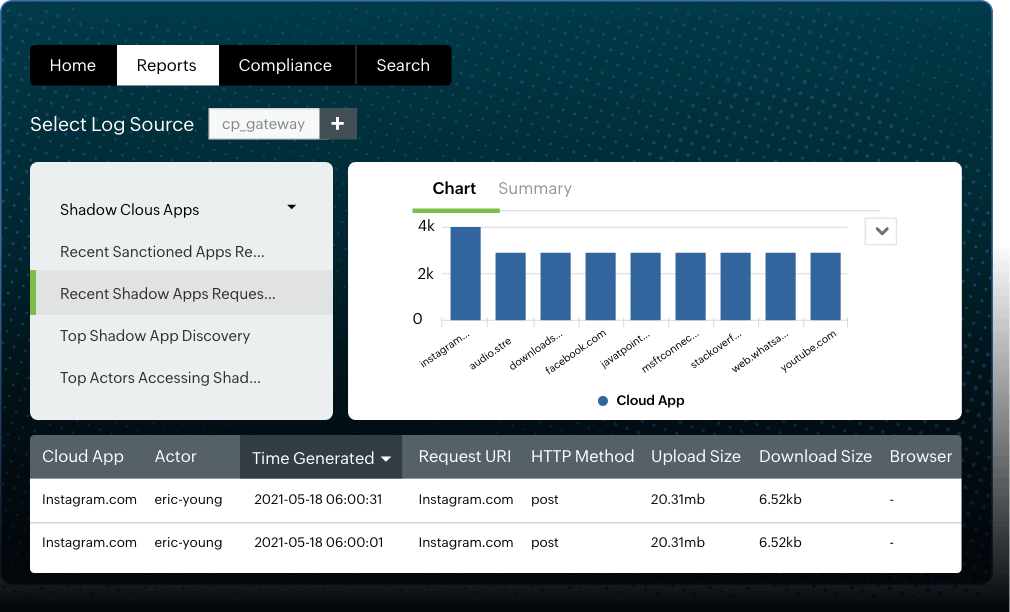
Applications used within your network without your security team's knowledge or approval (shadow applications) represent a significant security risk, as they bypass essential security measures.
With Log360 Cloud, you can monitor shadow IT application use and access, and also ban applications that can create security vulnerabilities.
© 2024 Zoho Corporation Pvt. Ltd. All rights reserved.
Curious to see this in action?
Sign up for Log360 Cloud!
Have an account already? Sign
in
© 2024 Zoho Corporation Pvt. Ltd. All rights reserved.